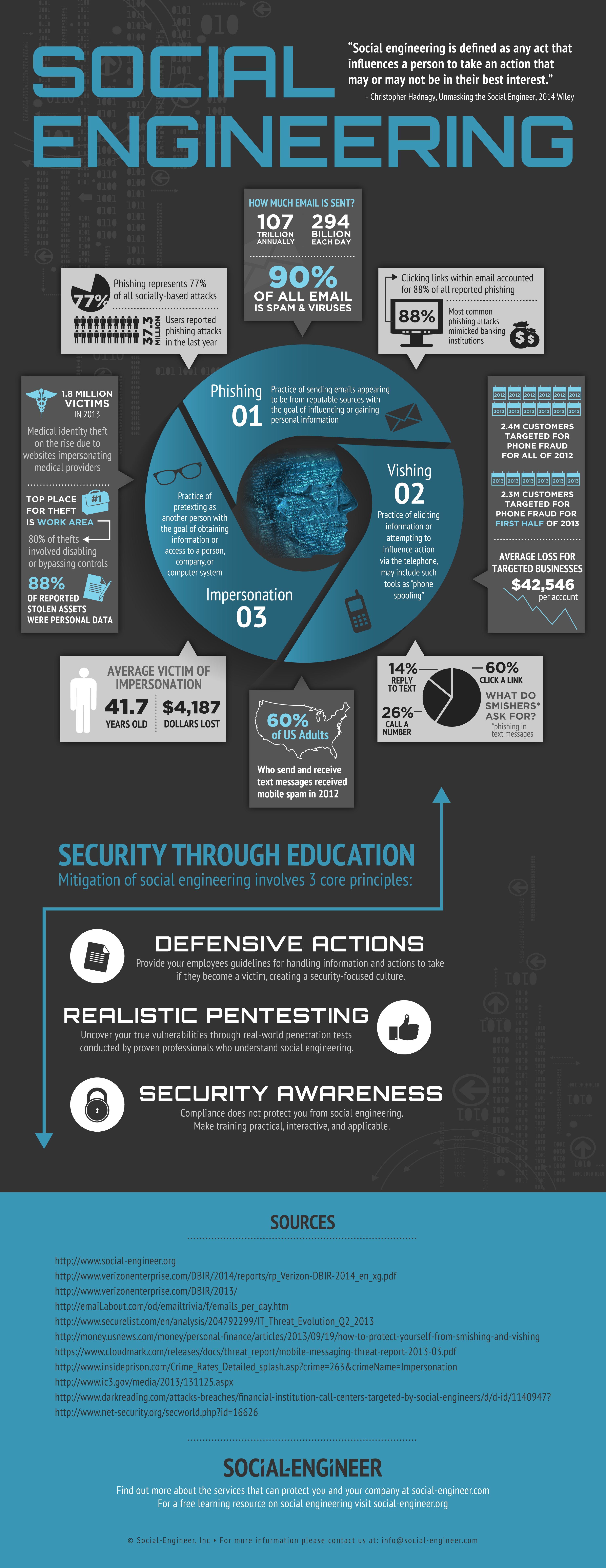
Some phishing emails can achieve a hit rate of 45 percent, says Google, while even the worst and most obvious scams can attract clicks from 3 percent of users (Nield, 2014). Considering there are little cost and effort associated with sending out 300,000 emails, at just a 3% hit rate, you can have 9000 victims. That is an incredibly high reward to risk ratio.
Understanding that good security is a multilayer approach, there are multiple layers of security that could potentially destroy an email phishing campaign. Some of these layers may include Email Gateway Spam Filters, Outlook ‘Junk Email’ Filters, Host-based Antivirus, Intrusion Prevention Systems, Web Proxy Servers, and Egress filtering (Zeknox, 2013).
While this approach offers a good amount of protection, there are as many tools available to help phishers bypass those layers.
Any phishing campaign begins with gathering email addresses. For this post, I’ve decided to discuss a few ways of gathering good target information for the best possible results.
Tools like Jigsaw (now owned by Salesforce) have legitimate uses for sales, however, they also offer a sensational database for those with criminal intent. As Jigsaw puts it:
“Jigsaw is a leading provider of business information and data services that uniquely leverages user-generated content contributed by its global business-to-business community of 1.5 million members. Jigsaw gives individuals and companies access to business contact information for 24 million business professionals and profiles of 4 million companies” (Crunchbase, 2010).
Another tool is called the harvester. It parses search engine data and pulls out email addresses (laranues, 2016).
Additionally, there is LinkedIn. By getting a paid membership you can specifically narrow down the scope of intended targets by the types of companies and positions within the companies they work for.
While this is certainly far from a conclusive list of methods to gather intel and valuable contact information, it is a good start to the discussion. A more targeted user list (Systems Administrators, C-level executives) provide both greater access to systems that can be exploited and better results for sculpting a message that will be clicked on.
David Nield (2014 Nov. 9). Phishing emails still surprisingly effective, reports Google. Retrieved from http://www.digitaltrends.com/computing/phishing-emails-still-surprisingly-effective-reports-google/
Crunchbase (2010 April 21) Jigsaw. Retrieved from https://www.crunchbase.com/organization/jigsaw#/entity
laramies (2016 April 18). theHarvester. Retrieved from https://github.com/laramies/theHarvester
Zeknox (2013 Jan 30). How do I phish? – Advanced Email Phishing Tactics. Retrieved from https://www.pentestgeek.com/phishing/how-do-i-phish-advanced-email-phishing-tactics
